NeQter Labs FAQ
Office 365 Questions
How does NeQter retrieve Office 365 event logs?
After the user has registered an application in their Azure portal and granted it permission to read audit logs, NeQter utilizes the credentials of the application to retrieve access tokens. These access tokens are used to periodically query the Office 365 Management APIs on behalf of the registered application to retrieve new event logs. While we do store these credentials locally in order to retrieve access tokens, the application and NeQter’s access to your Office 365 event logs can be invalidated at any time by revoking the application’s permissions, deleting the application, or disabling the service.
Are event logs retrieved in real-time (as they occur)?
No, our service retrieves event logs for the configured options periodically. This is done because there is a variable lag time between the occurrence of actions and events. This also takes into account when these logs become available to retrieve from Microsoft’s APIs. This period can range between several minutes and multiple days.
Why don’t I see any logs after configuring and enabling the service?
Ensure that you have enabled auditing for your organization. This document explains how to complete this process.
Additionally, when the service is enabled it creates subscriptions for the content types you have chosen. According to Microsoft’s documentation, it may take up to 12 hours for newly created subscriptions to begin populating with event logs. This is due to the process of logs being collected and aggregated across multiple servers and data centers. If you still don’t see any retrieved logs after this period has passed you should contact our support team.
Why do some logs not appear until days after the event occurred?
This may occur infrequently due to temporary outages or other issues with Office 365. In this case, Microsoft attempts to backfill any logs that may have been dropped, potentially resulting in a delay of multiple days.
Why do some events generate multiple event logs?
Unfortunately, this appears to be a result of the distributed nature of Office 365. Some events or actions may generate multiple event logs (e.g. this can often be seen with “UserLoggedIn” event logs), but this is not always the case. The content of the logs remains useful for detecting trends and anomalies.
How do I revoke NeQter’s access to my Office 365 event logs?
Disabling the service from within NeQter’s settings will remove the credentials associated with the application registered in your Azure portal. It will prevent your NeQter device from any further polling of the Office 365 Management APIs. Additionally, while the service will still attempt to retrieve logs, deleting the registered application or revoking the required permissions from it will also prevent NeQter from being able to retrieve event logs.
GSuite Questions
How does the Event Retrieval Module access my G Suite domain?
We use the OAuth standard to retrieve audit logs through Google’s Reports API. This means that you grant access to our service to retrieve information through Google’s API by logging into your G Suite domain and accepting the request. Google grants our application a token which can then be used to retrieve audit reports. Our service is never made aware of, nor stores your credentials, and we are unable to view any details concerning your G Suite account or domain. We only store the OAuth token that is generated after authentication and authorization. This token can then be invalidated or removed at any time by revoking access to our application or disabling the service.
Is NeQter Labs able to view retrieved event logs?
No, we don’t have access to the retrieved event logs. For more information, please refer to our privacy policy.
Are event logs retrieved in real-time (as they occur)?
No, our service retrieves event logs for the configured audit report options periodically. This is done because G Suite audit logs aren’t made available in real-time, and experience lag times before event data is available to retrieve. Depending on the audit report option, this lag time may range from several minutes to a couple of hours.
Why are there multiple event logs with the same timestamp?
For certain types of audit reports, such as Drive events, a single event may contain multiple sub-events. For instance, if a file is moved to a new folder its permissions may also change, which would generate multiple events from the initial action. Consequently, multiple events logs may be generated from a single event, each with the same timestamp.
Can any user in my G Suite domain grant access to the Event Retrieval Module to retrieve audit logs?
It is possible to complete the authentication and authorization process with any valid Google Apps account. However, if the user isn’t an administrator of the G Suite domain, the service will be unable to retrieve any audit report event logs. Additionally, at this time we only support the completion of the authentication and authorization process by a single user per instance of the Event Retrieval Module.
How do I revoke the Event Retrieval Module’s access to my audit reports?
Simply disabling the service will remove the token used to access your audit report logs and prevent further access. The authentication and authorization process must be completed again for the service to regain access.
To fully revoke access, you should also remove the permission granted to the application in your Google account settings. This can be done by:
Navigating to the Google account settings for the account used to grant access to the application
Select Sign-in & Security > Apps with account access > Manage apps
Select the NeQter Labs - Event Retrieval Module and then click ‘Remove Access’
This process can also be completed through the Administrator Console by:
Navigating to the Administrator Console for your G Suite domain
Select Users, and then select the User used to grant access to the application
Select Security > Connected Applications
Hover over the NeQter Labs - Event Retrieval Module and then click the trashcan icon to remove access
I forgot my admin password and am not able to login!
If you forgot your credentials to access your admin account you can attempt to reset it via connecting to your NeQter Unit’s Console Terminal and resetting it there. You will need the default credentials again to log into your NeQter Unit which are as follows:
Default WebUI admin account credentials:
Username: admin@neqter.local
Password: Admin
The console terminals default credentials are as follows if they have not been changed as well:
Username: neqter
Password: neqter
Once you are logged into the console, you will find one of the options to be Restore Administrator User, click this to restore default credentials for your Admin account. Once done you can use the WebUI account credentials to log into the NeQter Unit.
NOTE: This only works if your Console Terminal Password has also not been changed
What ports /URLs are used by the NeQter Appliance?
The ports below are used by our NeQter Appliance and should have traffic allowed.
Incoming Ports
Port # Use 22 SSH 514 SYSLOG 5000 WebUI 5001 Agent Manager 5045 Agent 6514 Secure Syslog 8444 Vulnerability Scanner WebUI
NOTE: For Port 22 you will only need it open if a Support Remote Session requires access to the backend of the device, outside of this specific circumstance it can remain closed.
Outgoing Ports
Port # Use 443 HTTPS / License & Update Server 873 Vulnerability Scanner Feed 8443 License / Update Server
NOTE: For Port 8443 it is only outgoing for versions 2.3 and below.
Web URLs
URL Use updates.neqterlabs.com Update / License Server for NeQter Device feed.neqterlabs.com Vulnerability Scanner Feed Update1
1
. Vulnerability scan feeds are used to update CVEs, NVTs, CPEs and other bundles needed to keep NeQter up to date with latest vulnerabilities.
Vulnerability Scanner Overrides not Applying?
Be sure to have a filter created with Apply Overrides for the desired report/result requiring them and say yes. You can do this by first going to the Report(s) or Results Page you’d like to see the overrides applied to. Once on the page you’d like to apply overrides to, go to the top right and click the Edit Filter button (looks like a piece of paper with a pencil on it).
Now you should be in the Update Filter window which from there you will need select Yes next to the Apply Override option. You will then need to check off the Store filter as checkbox and type in a name for your new filter in the text box right next to it. When you’ve done all of that click the Update button and your new override should be able to apply. You can enable this filter by clicking the drop down menu on the top right and selecting the filter you created.
How to stop shortcuts from appearing on devices when using the MSI File?
Step 1.
Open the MSI File with an MSI Editor such as Orca.
Step 2.
Go to the MSI File’s Properties table and add the following field (you can add a field on Orca by double clicking an empty box).Field: ADDDESKTOPICON
Value: 0
Step 3.
Navigate to the MSI File’s Shortcuts table and delete the MyDesktop… field.
Step 4.
Click on the Save icon to save the changes you just made.
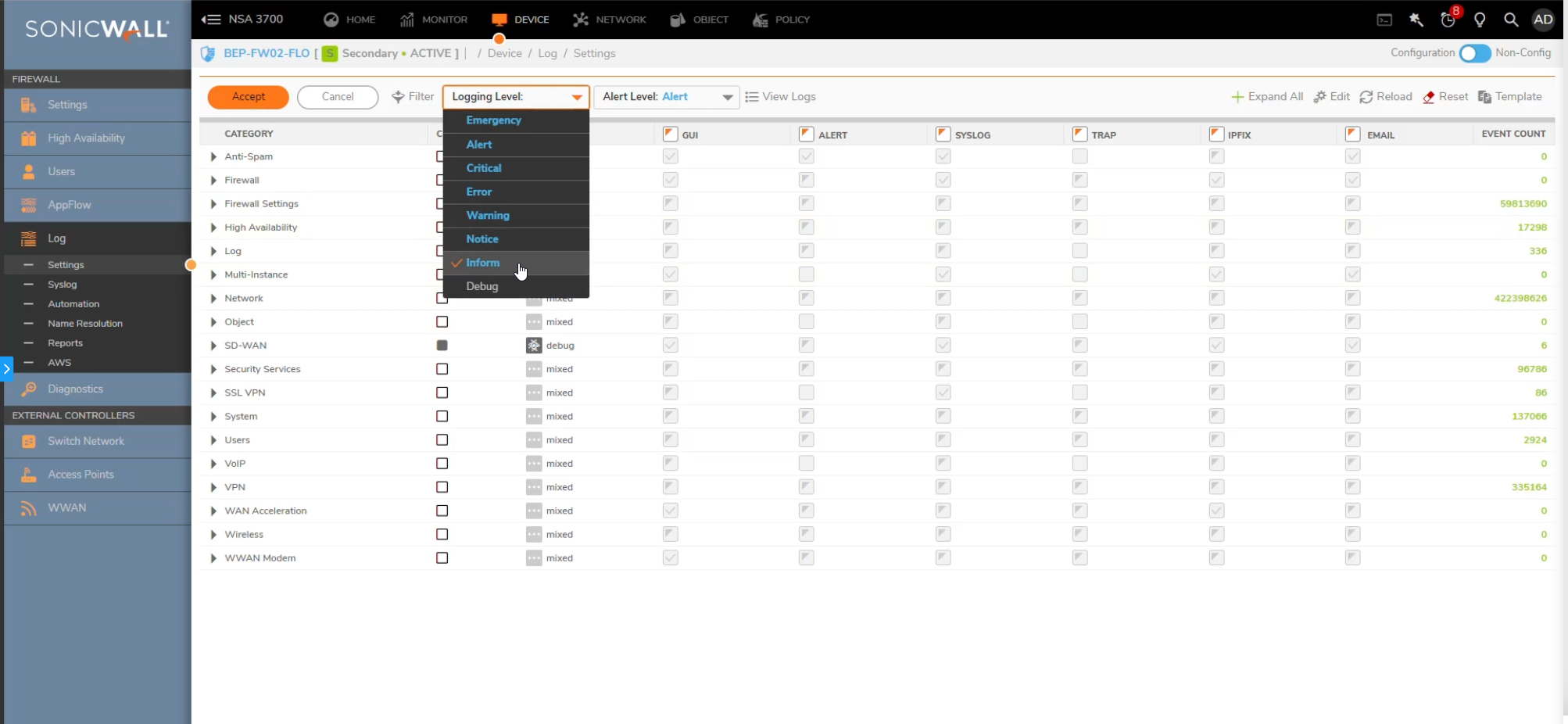
Some information in sonicwall is missing
On newer sonicwalls there might be certain important information changed from baseline notice severity to information. We suggest changing the severity level back to notice if this occurs, especially after an update. Below is an example image:
How to retrieve agent logs from an external device not connected to a local network via VPN?
If you have remote workers that do not frequently connect to your companies VPN you may need to configure port forwarding on your firewall in order for remote agents to communicate with the NeQter appliance.
Considerations:
- We recommend sending logs to the NeQter appliance via VPN rather than performing a port forward. Only setup port forwarding if your remote workers are not required to connect to your VPN to work.
- Port forwarding will expose a set of ports on your NeQter appliance to the internet.
- You may experience issues if your physical location does not have a static public IP address. If your IP changes the agents will lose communication and will need to be manually re-configured to use the new IP.
- You can type “Whats my IP” into google to discover your public IP address. This will provide you with the public IP address that you are using to browse the internet.
Port forwarding can be configured in your firewall’s management interface. You may need to visit your firewall vendor’s documentation for instructions on how to configure port forwarding for your firewall.
- Configure port forwarding of ports 5000, 5001, and 5045 from your public address to your NeQter’s internal address.
- Have the NeQter agents configured to send to your public IP address.
If the logs are being sent via agents then data should be seen under the Host tool if working properly.
NOTE: These are general guidelines for configuring a Port Forwarding rule. If you are still unsure about the process we suggest talking with your MSP and/or service provider for further help.
How does NeQter identify users on its system?
Users are identified by a UUID that is generated on user creation & are never reused. If a user is deleted the creation of a user with the same email address will not result in the same UUID. In turn, UUIDs are never changed for a user account through its life even if the email, user credentials or other attributes of the user account are changed.